Introduction
In today’s digital age, cybersecurity is paramount. As cyber threats continue to evolve, it’s crucial for individuals and organizations to stay informed about potential vulnerabilities and attacks. In this blog post, we’ll explore ten critical cybersecurity threats, ranging from common exploits like SQL injection to more sophisticated techniques like Clickjacking. Understanding these threats is the first step toward defending against them.
1. Brute Force Attacks
Brute force attacks represent one of the most basic yet persistent threats in the cybersecurity landscape. In a brute force attack, malicious actors attempt to gain unauthorized access to a system or an account by systematically trying every possible combination of usernames and passwords until they stumble upon the correct one. While these attacks can be time-consuming and labor-intensive, they are often successful when targeted accounts have weak or easily guessable passwords. Attackers can deploy automated tools to speed up the process, making it even more critical for individuals and organizations to bolster their defenses.
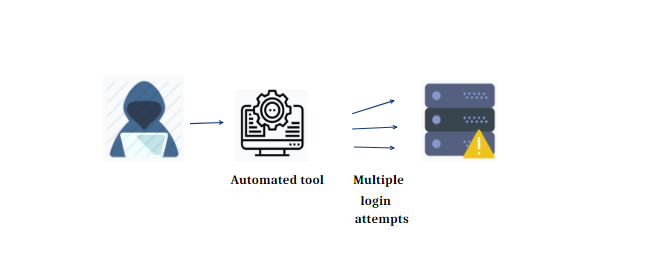 To protect against brute force attacks, it is essential to enforce strong password policies that encourage users to create complex and unique passwords. Implementing account lockout policies can also be effective, automatically locking an account after a certain number of failed login attempts. Additionally, consider implementing multi-factor authentication (MFA) wherever possible. MFA adds an extra layer of security, requiring users to provide not only a password but also a second form of verification, such as a fingerprint or a one-time code from a mobile app. This significantly reduces the success rate of brute force attacks.
To protect against brute force attacks, it is essential to enforce strong password policies that encourage users to create complex and unique passwords. Implementing account lockout policies can also be effective, automatically locking an account after a certain number of failed login attempts. Additionally, consider implementing multi-factor authentication (MFA) wherever possible. MFA adds an extra layer of security, requiring users to provide not only a password but also a second form of verification, such as a fingerprint or a one-time code from a mobile app. This significantly reduces the success rate of brute force attacks.
2. CSRF Vulnerability
Cross-Site Request Forgery (CSRF) is a deceptive and potentially dangerous form of cyberattack. In a CSRF attack, a malicious website tricks a user’s browser into making an unwanted and often harmful request to a different site, usually one where the victim is already authenticated. Since the request comes from the victim’s browser, the target website may mistakenly consider it legitimate. The consequences can be severe, ranging from unauthorized actions, such as changing a password or making financial transactions, to data theft or manipulation.
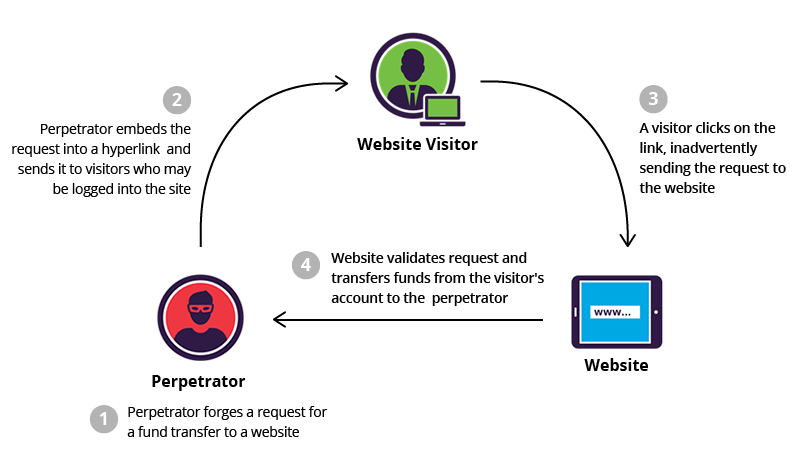 Protecting against CSRF vulnerabilities requires developers to implement several security measures. One common defense is the use of anti-CSRF tokens, which are unique tokens generated for each user session and included in the HTML forms or AJAX requests. When a request is made, the server checks if the token matches the expected value, rejecting any requests with incorrect or missing tokens. Additionally, web applications should validate the source of incoming requests and implement the “SameSite” attribute for cookies to limit their scope. Educating users about CSRF and advising them to log out of sensitive accounts when not in use can also reduce the risk of these attacks. Being proactive in addressing CSRF vulnerabilities is crucial in today’s interconnected online world.
Protecting against CSRF vulnerabilities requires developers to implement several security measures. One common defense is the use of anti-CSRF tokens, which are unique tokens generated for each user session and included in the HTML forms or AJAX requests. When a request is made, the server checks if the token matches the expected value, rejecting any requests with incorrect or missing tokens. Additionally, web applications should validate the source of incoming requests and implement the “SameSite” attribute for cookies to limit their scope. Educating users about CSRF and advising them to log out of sensitive accounts when not in use can also reduce the risk of these attacks. Being proactive in addressing CSRF vulnerabilities is crucial in today’s interconnected online world.
3. Clickjacking Vulnerability
Clickjacking is a sophisticated but insidious attack that exploits the trust users have in a legitimate website. In a clickjacking attack, the attacker overlays a malicious webpage element on top of a legitimate website, effectively tricking users into clicking on hidden buttons or links. Since the user believes they are interacting with the genuine site, they unknowingly perform actions they didn’t intend, such as liking a post, sharing sensitive information, or even initiating financial transactions.
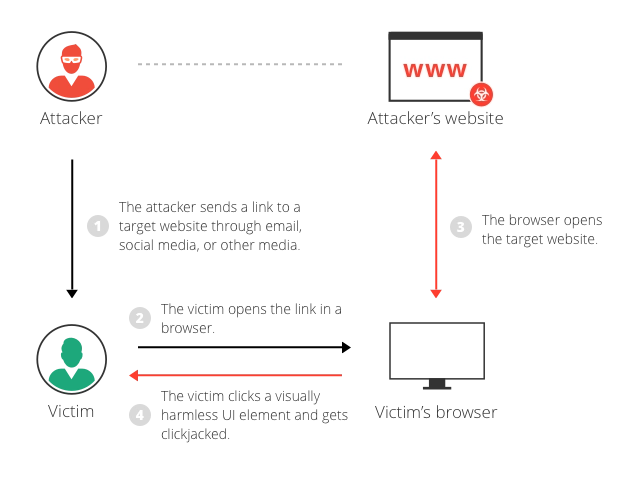 To defend against clickjacking, web developers should implement frame-busting scripts that prevent their site from being loaded within frames or iframes on malicious pages. Additionally, security headers like the “X-Frame-Options” and “Content Security Policy” (CSP) can help mitigate this threat by controlling how a website can be embedded or framed.
To defend against clickjacking, web developers should implement frame-busting scripts that prevent their site from being loaded within frames or iframes on malicious pages. Additionally, security headers like the “X-Frame-Options” and “Content Security Policy” (CSP) can help mitigate this threat by controlling how a website can be embedded or framed.
4. Long Password DoS Attack
Long password denial-of-service (DoS) attacks exploit a vulnerability in the handling of excessively long input data, overwhelming a system’s resources and causing it to become unresponsive. While not directly compromising data or security, these attacks can disrupt services and impact the availability of a system.
 Here is an example for Long Password DoS
To defend against long password DoS attacks, developers should implement input validation and limits for user inputs. By setting reasonable boundaries on input length, systems can protect themselves from resource exhaustion and maintain operational efficiency.
Here is an example for Long Password DoS
To defend against long password DoS attacks, developers should implement input validation and limits for user inputs. By setting reasonable boundaries on input length, systems can protect themselves from resource exhaustion and maintain operational efficiency.
5. Client-Side Validation Bypass Vulnerability
Client-side validation is a helpful tool for improving user experience, but it should never be relied upon for security. Attackers can manipulate client-side validation to bypass security measures and submit malicious data to a server. The solution is to always perform server-side validation. This ensures that no matter what the client sends, the server enforces data integrity and security. By incorporating server-side validation, you can prevent malicious inputs from reaching your application logic and compromising your system.
6. SQL Injection
SQL injection remains a prevalent threat in the cybersecurity landscape. Attackers exploit vulnerable input fields to inject malicious SQL queries, potentially gaining unauthorized access to a database or manipulating data. Protecting against SQL injection involves using parameterized queries and input validation.
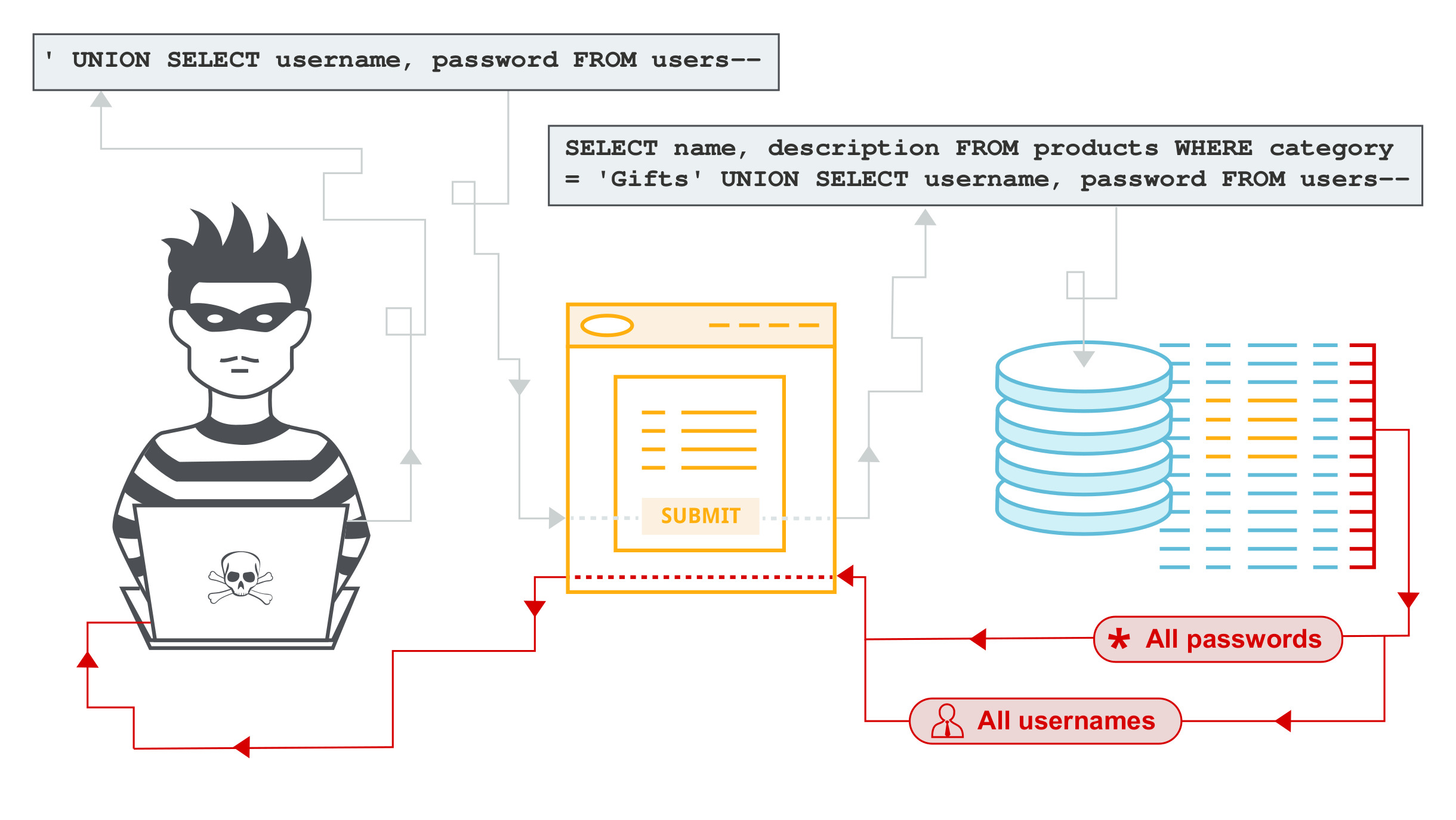 Parameterized queries separate user inputs from SQL commands, making it impossible for attackers to inject malicious code. Comprehensive input validation ensures that only safe, expected data enters the system, reducing the risk of SQL injection.
Parameterized queries separate user inputs from SQL commands, making it impossible for attackers to inject malicious code. Comprehensive input validation ensures that only safe, expected data enters the system, reducing the risk of SQL injection.
7. Broken Authentication
Broken authentication vulnerabilities often result from lax security practices and can lead to unauthorized access to user accounts. To mitigate this threat, implement strong authentication mechanisms, such as multi-factor authentication (MFA), to ensure that only authorized users can access sensitive data. Secure session management is also crucial, as it prevents attackers from hijacking active sessions or using stolen credentials to gain access.
8. Rate Limit Issues
Failure to implement proper rate limiting can expose your application to various attacks, including brute force and DoS attacks. Rate limiting restricts the number of requests a single user or IP address can make in a given time frame, preventing excessive traffic that could disrupt services. By carefully configuring rate limits, you can protect your system’s availability and maintain optimal performance.
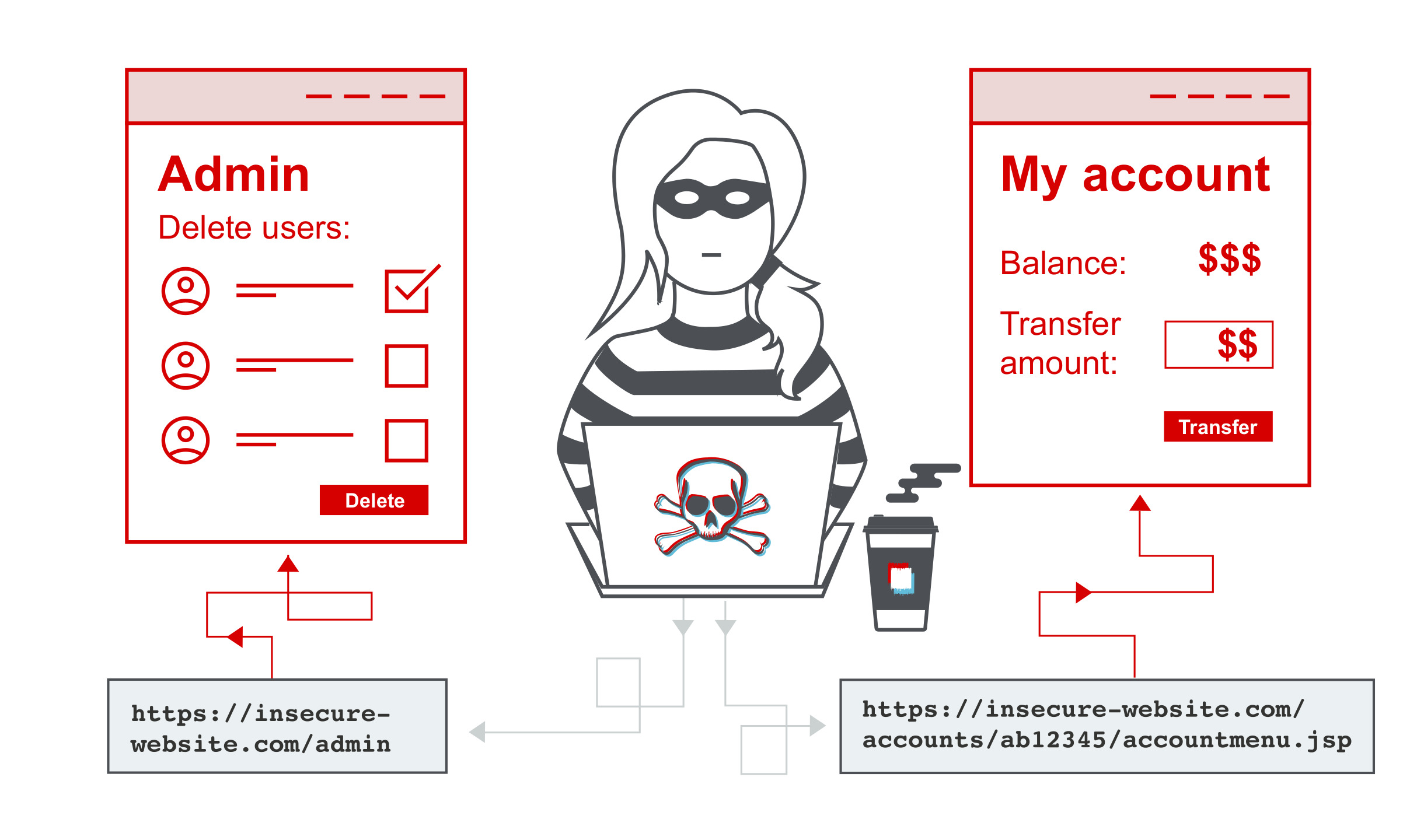
9. Broken Access Control
Broken access control vulnerabilities occur when users gain unauthorized access to restricted resources or perform actions they shouldn’t. Enforce proper access controls and authorization checks throughout your application to prevent unauthorized access to sensitive data. Role-based access control (RBAC) and regular security audits are essential components of a robust access control strategy. By addressing these vulnerabilities, you can ensure that your application only grants access to authorized users and maintains the confidentiality and integrity of your data.